EC Council Certified Ethical Hacker v9.0 [2016, ENG]
CBT Nuggets | Duration : 19:34:42 | .MP4 | English | Video: 1280x720 | Audio: 22.05 KHz, AAC LC, 2 ch, ~64.0 Kbps | Update June 2017 | 4.67 GB
Genre: eLearning
This Certified Ethical Hacker (CEH) v9.0 video training course teaches you the ethical hacking tools and techniques needed to improve your network's security posture. CBT Nuggets trainer Keith Barker walks you through building your own practice lab, including using evaluation software, and encourages you to not only watch and enjoy the videos, but practice everything hands-on in your own lab environment.
Recommended Experience
Networking fundamentals (CompTIA Network+ level of knowledge or better)
Familiarity with multiple versions of Windows
Familiarity with Linux is not necessary but recommended
Familiarity with VMware Workstation
Knowledge of Networking and Security at the CompTIA Network+ and Security+ levels, or better
Recommended Equipment
Host running VMware Workstation, that can support 64bit VMs.
Related Certifications
Certified Ethical Hacker v9 (#312-50)
Related Job Functions
Network/System Administrators/Engineers
Security officers
Auditors
Security professionals
Site administrators
Those concerned about the security of the network infrastructure
Keith Barker has been a CBT Nuggets trainer since 2012 and working with networking and security since 1985. Keith holds several security-related certifications including Cisco CCIE Security, Palo Alto CNSE, Check Point CCSA, CISSP and more.
EC-COUNCIL® and C|EH® are registered trademarks International Council of E-Commerce Consultants.
1. Welcome (4 min)
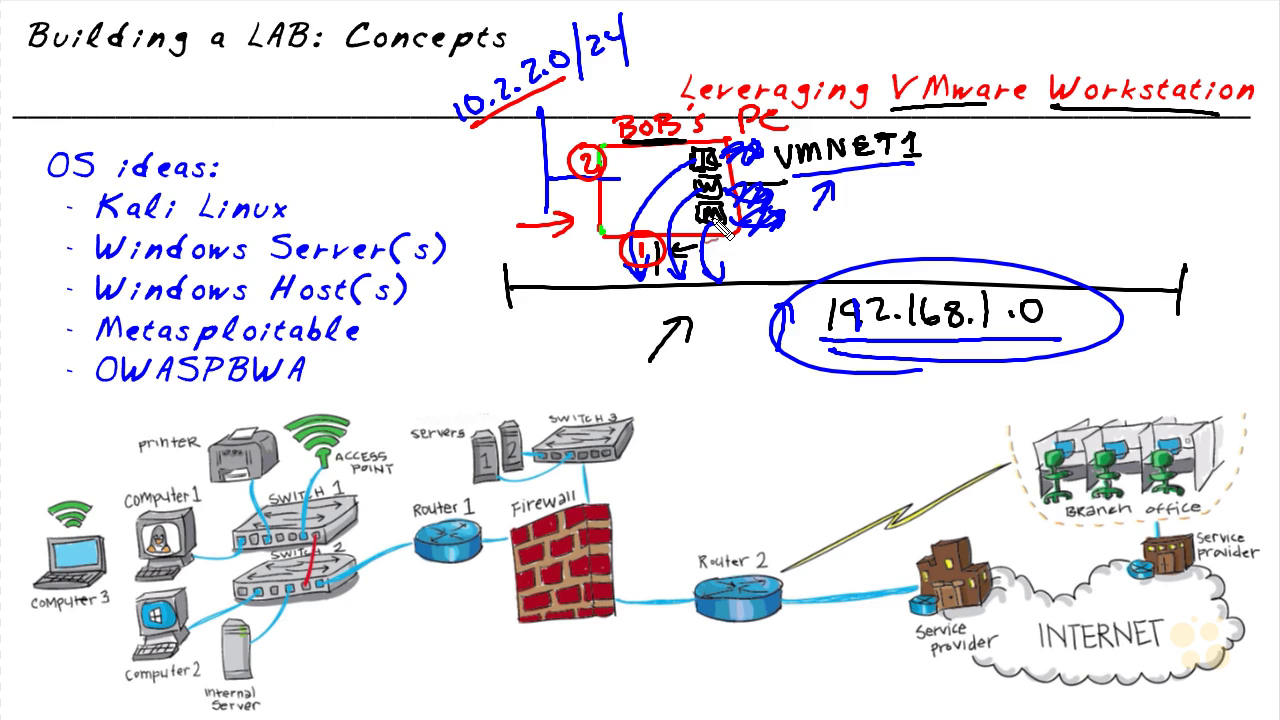
2. Building a LAB: Concepts (6 min)
3. Building a LAB: Networking (9 min)
4. Deploy a Kali Linux VM (14 min)
5. Adding Metasploitable to Your Lab (11 min)
6. Adding Windows to Your Lab (14 min)
7. Configure a Static IP on Kali (5 min)
8. Windows Evaluations (7 min)
9. Deploy Windows 8.1 (15 min)
10. Deploy Windows 2012 (11 min)
11. Deploy Windows 10 (7 min)
12. Deploy Windows 2016 (7 min)
13. Ethics and Hacking (10 min)
14. Hacking Vocabulary (6 min)
15. InfoSec Concepts (5 min)
16. Attack Categories, Types, and Vectors (5 min)
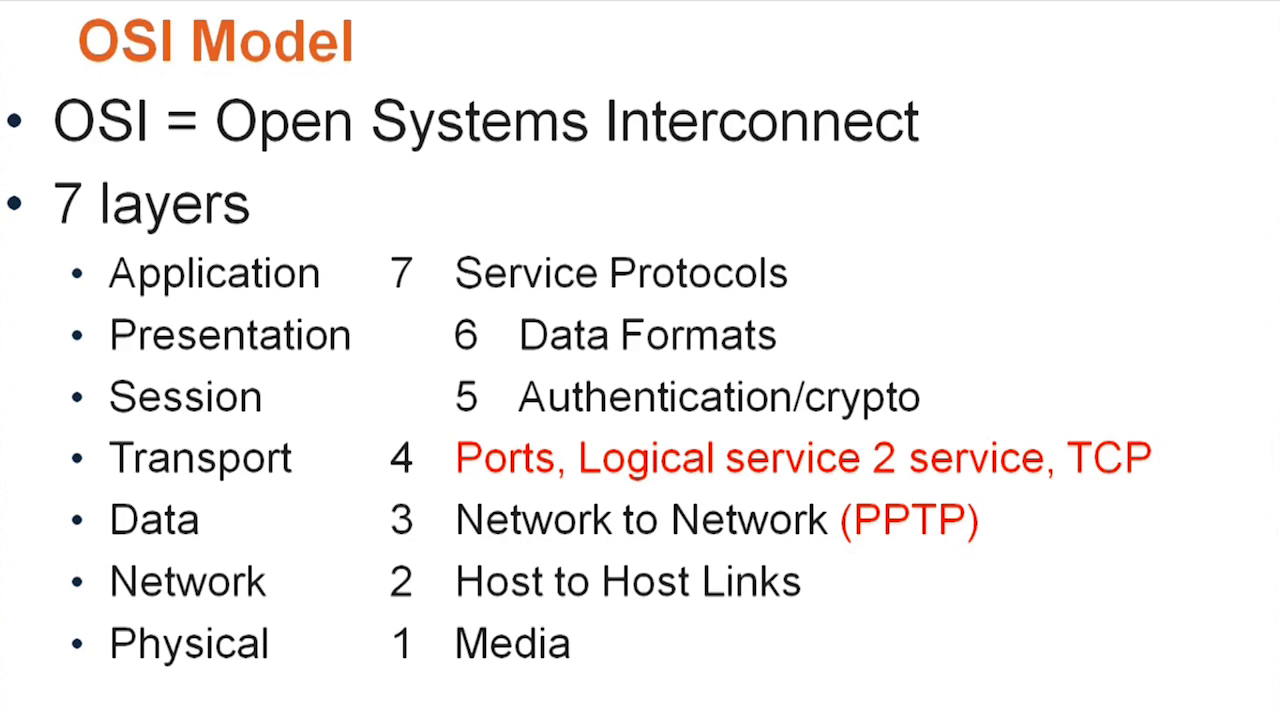
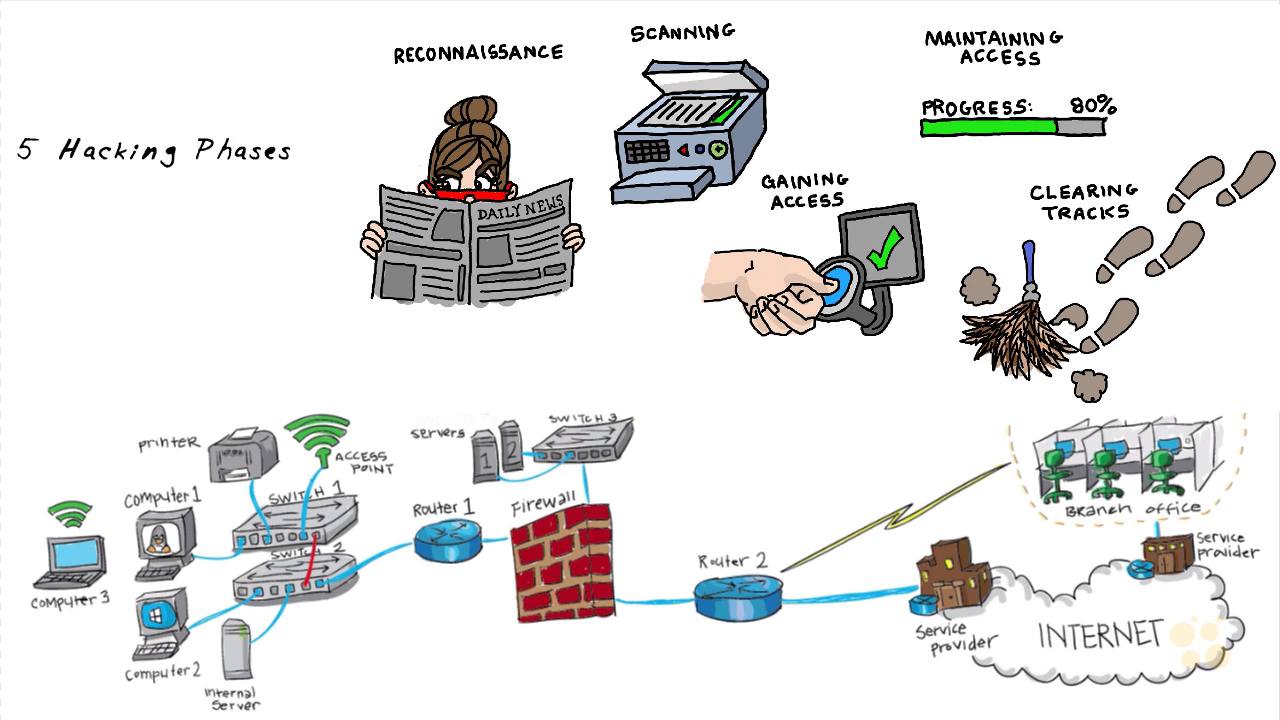
17. Five Phases of Hacking (5 min)
18. Footprinting and Reconnaissance Concepts (11 min)
19. Search Engine Tools (8 min)
20. Hacking using Google (12 min)
22. Metagoofil Metadata Tool (3 min)
23. Email Headers for Footprinting (5 min)
24. Using WHOIS for Recon (4 min)
25. DNS Tools (12 min)
26. Network Scanning Overview (3 min)
27. Network Scanning Methodology (9 min)
28. Port Discovery (11 min)
29. Network Scanning Tools (3 min)
30. Stealth Idle Scanning (10 min)
31. OS and Application Fingerprinting (10 min)
32. Vulnerability Scanning (8 min)
33. Network Mapping Tools (5 min)
34. Proxy Servers (8 min)
35. Using Public Proxy Services (6 min)
36. Enumeration Concepts (5 min)
37. NetBIOS Enumeration (11 min)
38. SNMP Enumeration Concepts (10 min)
39. SNMP Enumeration Tools (10 min)
40. LDAP Enumeration Concepts (5 min)
41. LDAP Enumeration Example (7 min)
42. NTP Enumeration (7 min)
43. SMTP Enumeration (8 min)
44. System Hacking Overview (9 min)
45. Password Cracking Concepts (10 min)
46. Password Attack Example: MITM and Sniffing (13 min)
47. Rainbow Crack Lab Setup (8 min)
48. Rainbow Crack Demonstration (8 min)
49. Password Reset Hacking (8 min)
50. DHCP Starvation (10 min)
51. Remote Access (15 min)
52. Spyware (9 min)
53. NTFS Alternate Data Streams Exploit (9 min)
54. Steganography with OpenPuff (7 min)
55. Steganography with SNOW (5 min)
56. Covering Tracks (7 min)
57. Malware Overview (10 min)
58. Trojan Overview (10 min)
59. Creating a Trojan (11 min)
60. Virus Overview (13 min)
61. Virus Creation (8 min)
62. Detecting Malware (17 min)
63. Malware Analysis (10 min)
64. Hash File Verification (8 min)
65. Sniffing Overview (12 min)
66. CAM Table Attack and Port Security (10 min)
67. DHCP Snooping (14 min)
68. Dynamic ARP Inspection (DAI) (14 min)
69. Social Engineering (15 min)
70. Denial of Service (DoS) Attacks (19 min)
71. Session Hijacking (18 min)
72. Hacking Web Servers (10 min)
73. Buffer Overflow (13 min)
74. OWASP Broken Web Application Project (13 min)
75. Shellshock (6 min)
76. SQL Introduction (9 min)
77. SQL Injection (16 min)
78. Web App Vulnerabilities: WordPress (10 min)
79. Wireless Hacking (18 min)
80. Using an Android VM (4 min)
81. Malware for Mobile (11 min)
82. Mobile Device Risks and Best Practices (13 min)
83. Firewall Evasion (19 min)
84. Firewall ACL Example (15 min)
85. NAT and PAT fundamentals (11 min)
86. IDS/IPS Evasion (17 min)
87. Honeypots (12 min)
88. Cloud Computing (23 min)
89. CIA: Confidentiality, Integrity, and Availability (3 min)
90. Policies (9 min)
91. Quantifying Risk (6 min)
92. Separation of Duties (13 min)
93. Symmetrical Encryption Concepts (14 min)
94. Asymmetrical Encryption Concepts (16 min)
95. Control Types (11 min)
96. Multifactor Authentication (12 min)
97. Centralized Identity Management (13 min)
98. Kerberos and Single Sign On (SSO) (17 min)
99. Backups and Media Management (9 min)
100. Operations Security Controls (14 min)
101. Physical Security Controls (11 min)
102. Incident Response (12 min)
103. VPNs (21 min)
104. Disaster Recovery Planning (13 min)
105. Pen Testing Tips (10 min)
106. Useful Tools (11 min)
107. Case Study (21 min)
108. Additional Resources and Exam Prep (8 min)
More Info
Recommend Download Link Hight Speed | Please Say Thanks Keep Topic Live