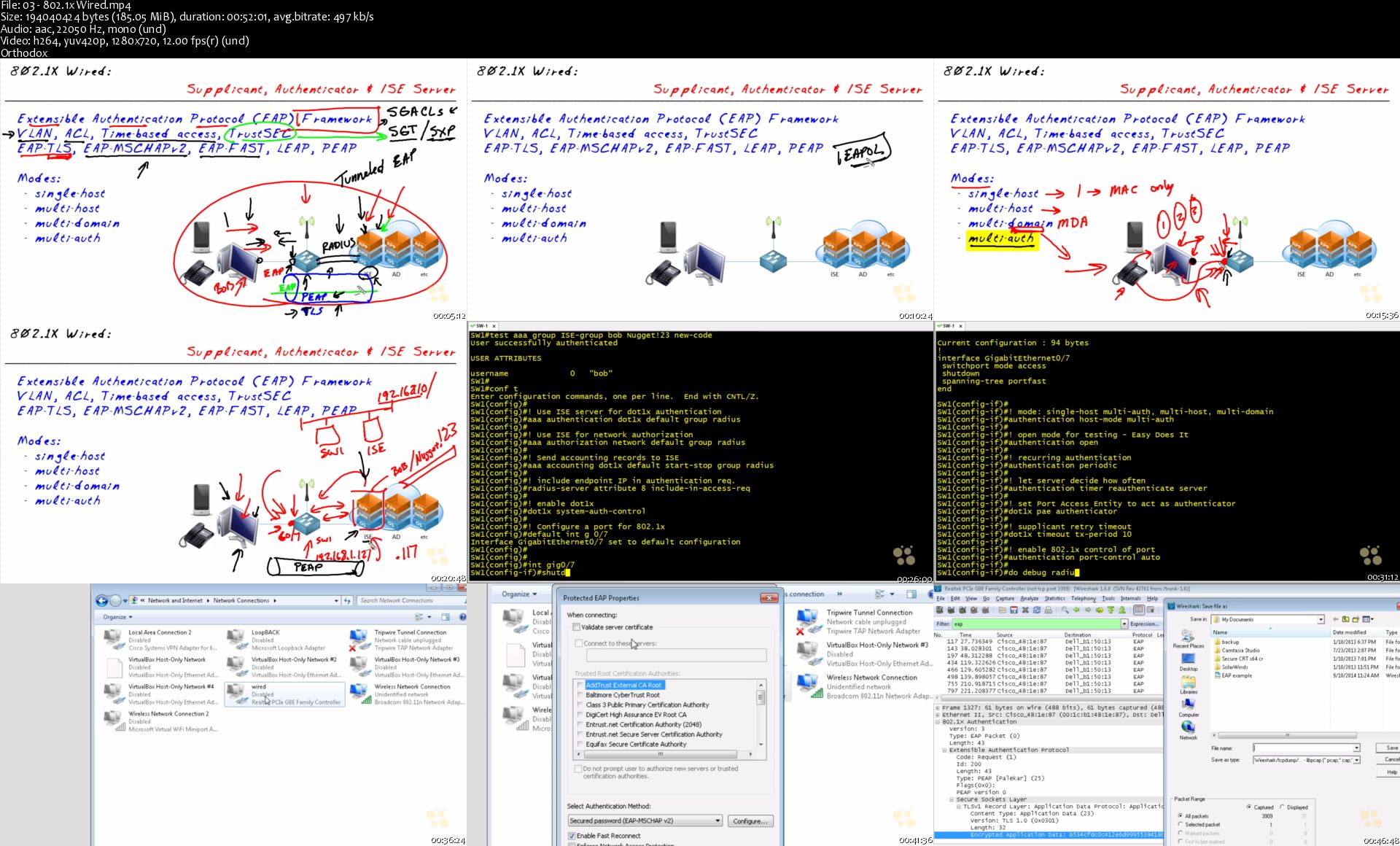
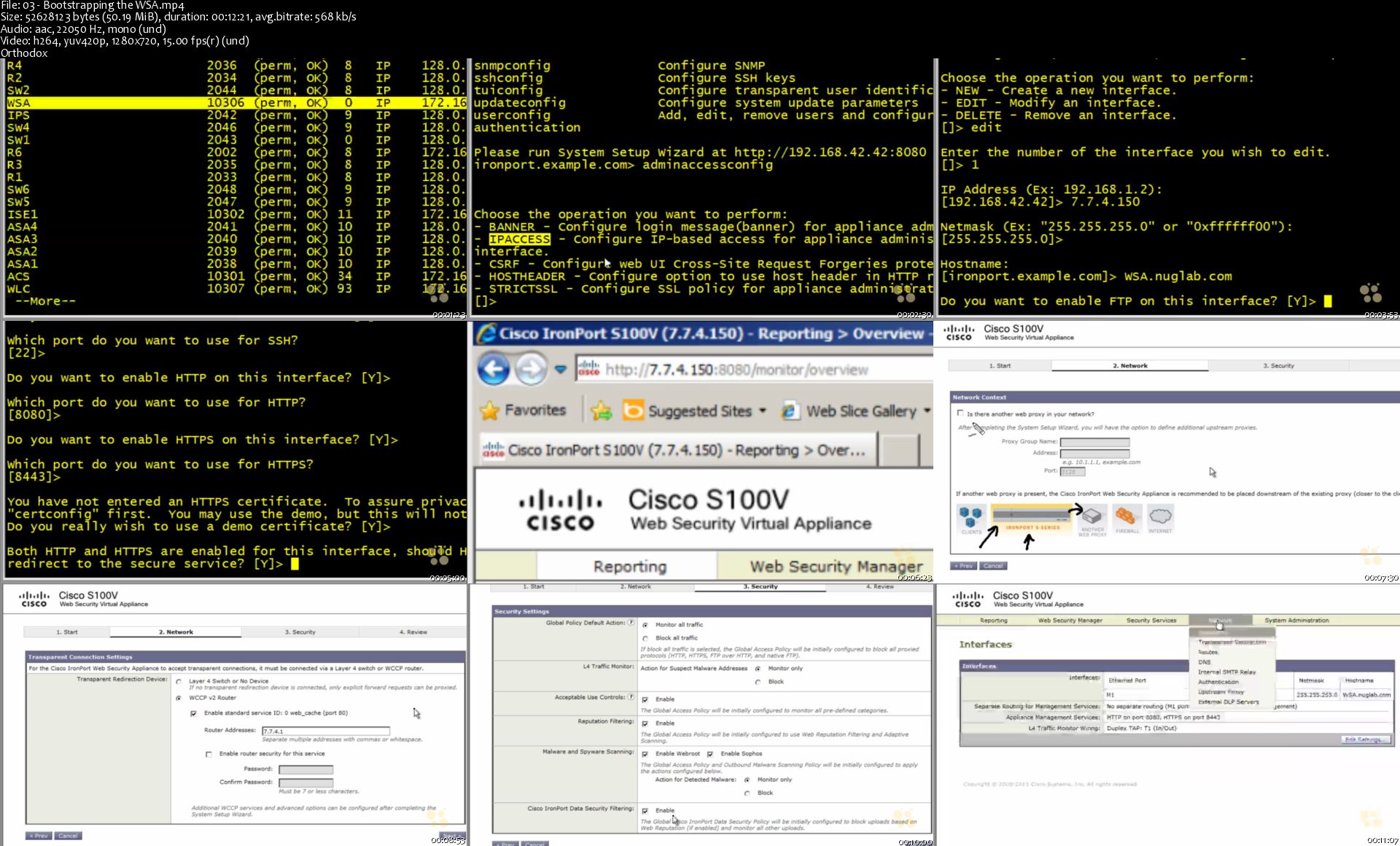
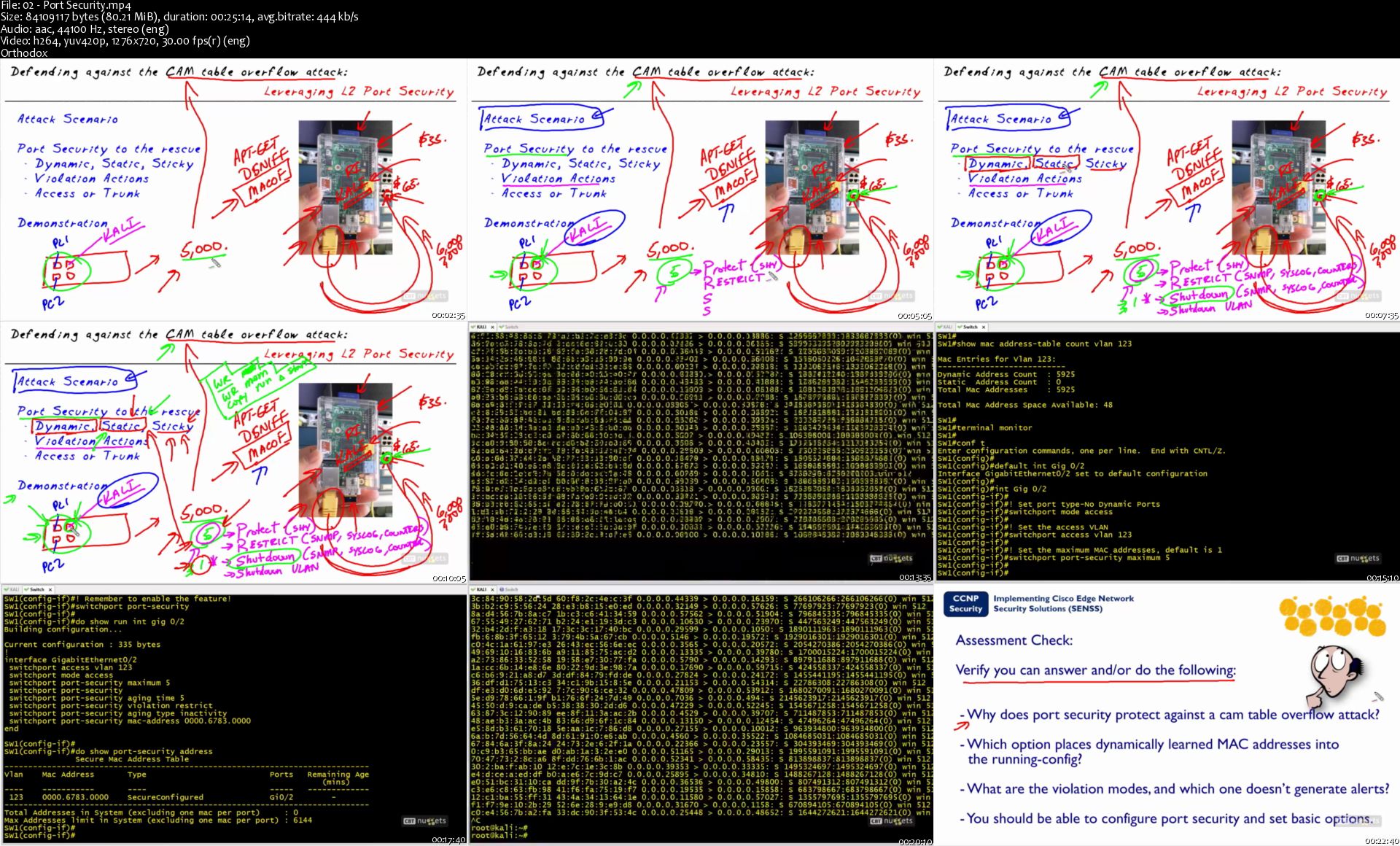
CBT Nuggets Cisco CCNP Security 300-209 SIMOS

CBT Nuggets Cisco CCNP Security 300-209 SIMOS
.MP4 | Video: 1280x720, 15 fps(r) | Audio: AAC, 22050 Hz, 2ch | 1.96 GB
Duration: 9 hours 14 minutes | Genre: eLearning Video | Language: English
This Implementing Cisco Secure Mobility Solutions (SIMOS) (300-209) course provides training on how to configure and implement a variety of Virtual Private Network (VPN) solutions on the Cisco ASA firewall and Cisco IOS software platforms. Topics include IKEv2, DMVPN, FlexVPN, GETVPN, and troubleshooting.
Related area of expertise:
Cisco security
Recommended skills:
CCNA Route/Switch and CCNA Security certification (or equivalent knowledge and skills)
Knowledge of Microsoft Windows
CCNA Security is a pre-requisite for the CCNP Security certification
Recommended equipment:
IOS that supports DMVPN, GETVPN and FlexVPN
IOS and ASA that support IKEv2
Related certifications:
CCNP Security. This course (SIMOS exam # 300-209) is part of the curriculum in the Cisco Certified Network Professional Security (CCNP© Security) certification
Related job functions:
Network Analyst
Network Engineer
Network Technician
Network Designer
Security Analyst
Security Auditor
Penetration Tester
Security Architect
Technical Manager
1. Welcome and Overview (00:06:36)
In this Nugget, Keith discusses the prerequisites that enable you to get the most from this course, and shares some tips for you to get the most out of this VPN-focused course.
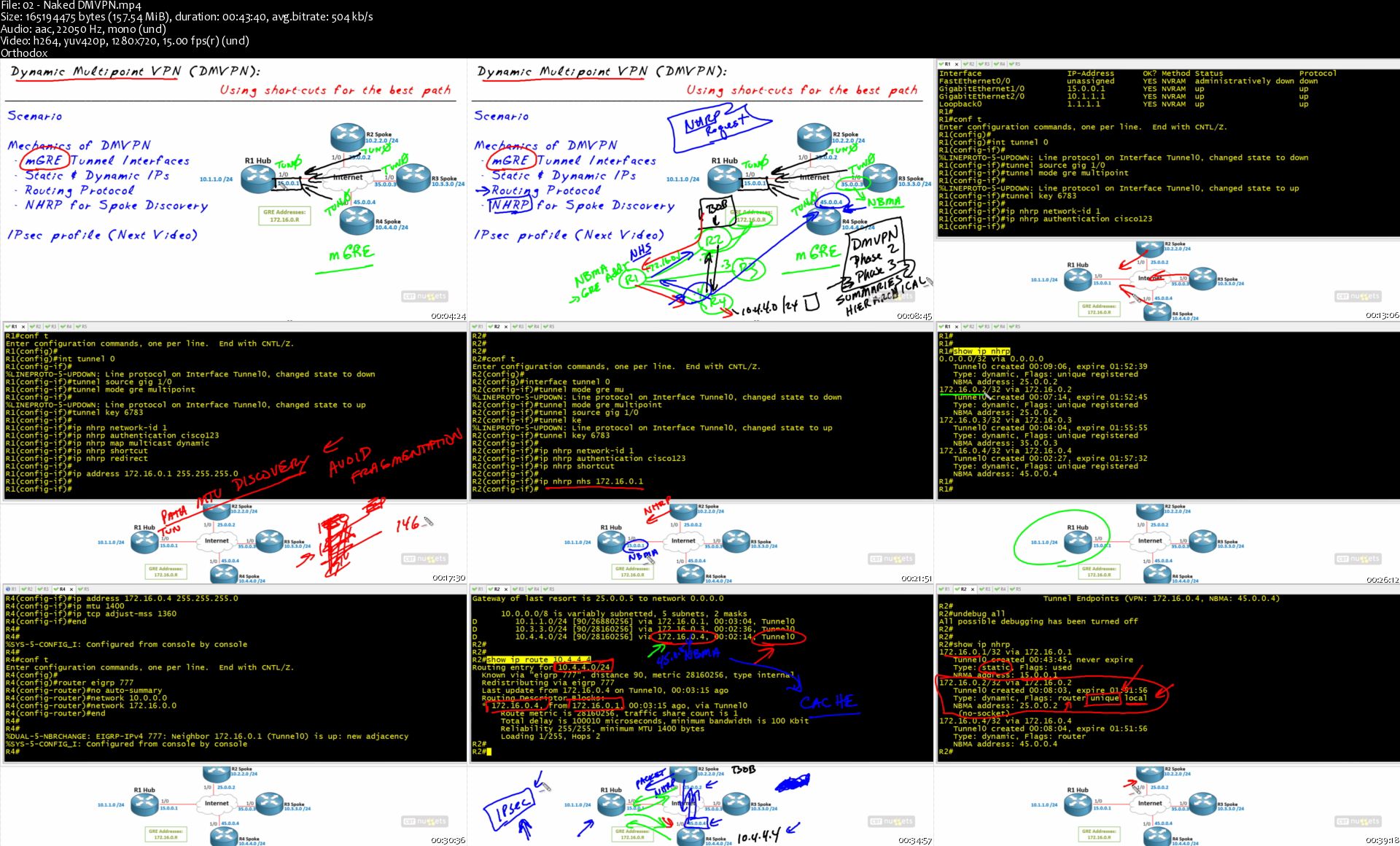
2. Naked DMVPN (00:43:40)
Dynamic Multipoint VPNs (DMVPNs) are a great way to set up full-mesh connectivity with manually setting up n(n-1)/2 static tunnels. In this Nugget, Keith talks with you about the core pieces that make up DMVPNs, including Next Hop Resolution Protocol (NHRP), multipoint GRE tunnel interfaces, dynamic routing protocols, and more. Configuration and verification also is included in this video. Adding IPsec to the DMVPN is covered in the next Nugget.
This video maps to "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
3. Protected DMVPN (00:32:17)
IPsec can be added to the DMVPN topology (and usually is) to provide encryption, authentication, and data integrity services for the packets traveling between the mGRE interfaces on the DMVPN routers. This Nugget presumes the viewer has viewed the previous Nugget in this course, "Naked DMVPN," and has a basic CCNA Security-level understanding of IKEv1 (IKEv1 and other cryptographic fundamentals can be reviewed in the CCNA Security course, specifically the videos "Cryptography Essesntials" and "IPsec Site to Site VPNs", which are part of the CCNA Security course).
This video maps to "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
4. TShoot DMVPN (00:37:23)
"What could go wrong?" These are the famous last words of the technician who didn't learn to identify and correct problems that can cause a DMVPN network to fail. In this Nugget, you join Keith to diagnose, troubleshoot and correct multiple problems in an existing DMVPN network.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
5. IKE Call Admission Control (00:25:17)
A brute force IKE attack, or even a malfunctioning system making multiple requests, can place a heavy load on the router, which may result in a Denial of Service (DoS) attack. In this Nugget, Keith chats about how IKE Call Admission Control (CAC) can be used to limit the number of IKE sessions that can be negotiated and set up on the router.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
6. VTI Site2Site VPNs (00:25:24)
Virtual Tunnel Interfaces (VTIs) are a simpler method of creating IPsec Site to Site tunnels (compared to traditional Crypto Maps), and VTIs offer the benefit of placing specific policies to either encrypted or clear-text traffic that is going through an interface. This Nugget discusses VTIs, and then demonstrates the configuration and verification of a VTI based static Site-to-Site VPN.
This video maps to the "Secure Communications" and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
7. Dynamic VTI Hub (00:23:54)
Using a Dynamic Virtual Tunnel Interface (DVTI), we can avoid the manual creation of multiple tunnel interfaces on the hub, but instead create a virtual template, and have the router automagically use that template to create individual virtual access interfaces on demand for IPsec sessions between it and the remote routers.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
8. FlexVPN Site2Site (00:37:49)
IKEv2 and the new methods of configuring the tunnels might take a bit of getting used to. In this Nugget, Keith helps ease that process by talking with you about the components of IKEv2 including policy, proposal, profile, and key ring. A demonstration of implementing IKEv2 on Cisco IOS is included as well.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
9. FlexVPN DVTI (00:09:12)
This Nugget explains some of the benefits of IKEv2, and demonstrates the conversion from a fixed tunnel interface to a virtual access interface using a virtual template and IKEv2.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
10. FlexVPN Smart Defaults (00:25:56)
Smart defaults can be used to save configuration time, and may be customized for your needs. In this Nugget, Keith demonstrates the defaults for (and customization of) the IKEv2 proposal, IPsec transform-set and IPsec profile.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
11. Certificate Install (00:29:19)
In this Nugget, Keith walks you through configuring an IOS router as a Certificate Authority (CA), as well as other routers becoming CA clients that will authenticate and enroll with the CA (using Simple Certificate Enrollment Protocol, SCEP) - in preparation for using their certificates as part of rsa-sig authentication.
This video maps to the "Secure Communications", and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
12. RSA-Sig IKEv2 Authentication (00:19:41)
Using digital certificates, peers who have a a common trusted CA, can authenticate and use the peer's cert and public key to verify the peer's digital signatures for the authentication of the IKEv2 tunnel. In this Nugget, Keith demonstrates this IKEv2 implementation. Supporting files are contained in the NuggeLab download associated with this course.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
13. DVTI IKEv2 Hub and Spoke RSA-Sig (00:16:56)
This Nugget demonstrates how to implement and verify the following: Dynamic Virtual Tunnel Interface (DVTI) on the Hub, Static Tunnel Interfaces on the Spokes, and IKEv2 with RSA-Sig for authentication. Configuration files, including the full final configs, are in the NuggetLab files associated with this course.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
14. IKEv2 Pushing Policy (00:12:51)
Adding network authorization and AAA can allows us to push policy down to VPN peers. This is implemented by creating a new (or modifying the default) IKEv2 authorization policy, and including that IKEv2 authorization policy in the IKEv2 profile.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
15. FlexVPN Clients (00:30:41)
Setting up a spoke as a FlexVPN "Client" allows opportunities for additional features including multiple peers for fault tolerance, and the pushing of networks based on the IKEv2 authorization policy configured. In this Nugget, Keith walks you through reconfiguring the spoke routers to be FlexVPN clients. The use of the IKEv2 authorization profile also is demonstrated to advertise routes between the FlexVPN client and server.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
16. Spoke 2 Spoke FlexVPN (00:32:59)
FlexVPN borrows the Next Hop Resolution Protocol (NHRP) from DMVPN to allow a hub and spoke topology to dynamically build spoke to spoke tunnels. The NuggetLab files contain all the configuration commands used in this video, along with the final working configuration for all four routers.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
17. FlexVPN Troubleshooting (00:20:18)
In this Nugget, Keith walks you through a troubleshooting scenario, leveraging show commands and pings to isolate the problems in a FlexVPN network.
This video maps to the "Troubleshooting, Monitoring, and Reporting Tools" section of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
18. GETVPN (00:50:45)
Group Encrypted Transport VPN (GETVPN) overcomes the delays often associated with creating a spoke-to-spoke tunnel, as there are no formal IPsec tunnels created between group members. In this Nugget, Keith explains and then demonstrates the implementation and verification of GETVPN.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
19. ASA 2 IOS IKEv2 (Site-to-Site IPsec VPN) (00:23:15)
In this Nugget, Keith explains and demonstrates the configuration on the ASA to support both IKEv1 and IKEv2 site-to-site tunnels, as well as configuring a peer IOS router. The router demonstration includes IKEv1 first, with the verification commands to confirm it is working, and then IKEv2 and verification once again that it is working.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
20. Verify and TShoot IPsec (00:07:29)
In this Nugget, Keith demonstrates where to look inside ASDM to verify or configure the IPsec Site-to-Site configuration implemented from the CLI in the previous video. Note: The following three videos are from the CCNP Security VPN v2.0 course, and it's recommended that you watch them before watching the next Nugget in this course.
ASA VPN Options Site to Site IPsec VPNs Troubleshooting IPsec Site-to-Site VPNs
This video along with the 3 assigned videos map to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
21. RA VPNs (00:12:17)
Remote Access (RA) VPNs play a critical role in secure mobility solutions. In this Nugget, Keith refers to some IOS VPN server documentation that may be useful for administrators of IOS based RA VPNs.
This video includes an assignment of watching the following videos from the CCNP Security VPNv2.0 course: VPN Profiles and Policies; Implementing Clientless SSL VPNs; AnyConnect SSL VPNs; Smart Tunnels and Plugins; AAA VPN Authentication; Troubleshooting Clientless SSL VPNs; Troubleshooting AnyConnect Client SSL VPNs; Cisco Secure Desktop and DAP; High Availability VPNs; and VPN Pieces and Parts.
These videos from the CCNP Security VPN v2.0 course are relevant for real-world experience, as well as the SIMOS 300-209 certification exam from Cisco. The list of assigned videos from this lesson also can be found in the NuggetLab files as a document named "Video Assignment.txt."
This video, along with the assigned videos, maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
22. AnyConnect Client Profile (00:14:24)
Whoever thought an XML file could be so powerful? In this Nugget, Keith demonstrates how to modify an AnyConnect Client Profile (the .xml file) on the ASA, and have that profile be automatically downloaded to AnyConnect Clients when they connect. This is an effective way to modify the AnyConnect client profile of remote systems using the ASA as a central distribution point.
This video maps to the "Secure Communications," "Troubleshooting," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
23. Closing Thoughts (00:15:33)
In this Nugget, Keith shares some tips for continued growth and success, along with some troubleshooting strategies.
This video maps to the "Secure Communications" and "Troubleshooting," sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
...

CBT Nuggets Cisco CCNP Security 300-209 SIMOS
.MP4 | Video: 1280x720, 15 fps(r) | Audio: AAC, 22050 Hz, 2ch | 1.96 GB
Duration: 9 hours 14 minutes | Genre: eLearning Video | Language: English
This Implementing Cisco Secure Mobility Solutions (SIMOS) (300-209) course provides training on how to configure and implement a variety of Virtual Private Network (VPN) solutions on the Cisco ASA firewall and Cisco IOS software platforms. Topics include IKEv2, DMVPN, FlexVPN, GETVPN, and troubleshooting.
Related area of expertise:
Cisco security
Recommended skills:
CCNA Route/Switch and CCNA Security certification (or equivalent knowledge and skills)
Knowledge of Microsoft Windows
CCNA Security is a pre-requisite for the CCNP Security certification
Recommended equipment:
IOS that supports DMVPN, GETVPN and FlexVPN
IOS and ASA that support IKEv2
Related certifications:
CCNP Security. This course (SIMOS exam # 300-209) is part of the curriculum in the Cisco Certified Network Professional Security (CCNP© Security) certification
Related job functions:
Network Analyst
Network Engineer
Network Technician
Network Designer
Security Analyst
Security Auditor
Penetration Tester
Security Architect
Technical Manager
1. Welcome and Overview (00:06:36)
In this Nugget, Keith discusses the prerequisites that enable you to get the most from this course, and shares some tips for you to get the most out of this VPN-focused course.
2. Naked DMVPN (00:43:40)
Dynamic Multipoint VPNs (DMVPNs) are a great way to set up full-mesh connectivity with manually setting up n(n-1)/2 static tunnels. In this Nugget, Keith talks with you about the core pieces that make up DMVPNs, including Next Hop Resolution Protocol (NHRP), multipoint GRE tunnel interfaces, dynamic routing protocols, and more. Configuration and verification also is included in this video. Adding IPsec to the DMVPN is covered in the next Nugget.
This video maps to "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
3. Protected DMVPN (00:32:17)
IPsec can be added to the DMVPN topology (and usually is) to provide encryption, authentication, and data integrity services for the packets traveling between the mGRE interfaces on the DMVPN routers. This Nugget presumes the viewer has viewed the previous Nugget in this course, "Naked DMVPN," and has a basic CCNA Security-level understanding of IKEv1 (IKEv1 and other cryptographic fundamentals can be reviewed in the CCNA Security course, specifically the videos "Cryptography Essesntials" and "IPsec Site to Site VPNs", which are part of the CCNA Security course).
This video maps to "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
4. TShoot DMVPN (00:37:23)
"What could go wrong?" These are the famous last words of the technician who didn't learn to identify and correct problems that can cause a DMVPN network to fail. In this Nugget, you join Keith to diagnose, troubleshoot and correct multiple problems in an existing DMVPN network.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
5. IKE Call Admission Control (00:25:17)
A brute force IKE attack, or even a malfunctioning system making multiple requests, can place a heavy load on the router, which may result in a Denial of Service (DoS) attack. In this Nugget, Keith chats about how IKE Call Admission Control (CAC) can be used to limit the number of IKE sessions that can be negotiated and set up on the router.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
6. VTI Site2Site VPNs (00:25:24)
Virtual Tunnel Interfaces (VTIs) are a simpler method of creating IPsec Site to Site tunnels (compared to traditional Crypto Maps), and VTIs offer the benefit of placing specific policies to either encrypted or clear-text traffic that is going through an interface. This Nugget discusses VTIs, and then demonstrates the configuration and verification of a VTI based static Site-to-Site VPN.
This video maps to the "Secure Communications" and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
7. Dynamic VTI Hub (00:23:54)
Using a Dynamic Virtual Tunnel Interface (DVTI), we can avoid the manual creation of multiple tunnel interfaces on the hub, but instead create a virtual template, and have the router automagically use that template to create individual virtual access interfaces on demand for IPsec sessions between it and the remote routers.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
8. FlexVPN Site2Site (00:37:49)
IKEv2 and the new methods of configuring the tunnels might take a bit of getting used to. In this Nugget, Keith helps ease that process by talking with you about the components of IKEv2 including policy, proposal, profile, and key ring. A demonstration of implementing IKEv2 on Cisco IOS is included as well.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
9. FlexVPN DVTI (00:09:12)
This Nugget explains some of the benefits of IKEv2, and demonstrates the conversion from a fixed tunnel interface to a virtual access interface using a virtual template and IKEv2.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
10. FlexVPN Smart Defaults (00:25:56)
Smart defaults can be used to save configuration time, and may be customized for your needs. In this Nugget, Keith demonstrates the defaults for (and customization of) the IKEv2 proposal, IPsec transform-set and IPsec profile.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
11. Certificate Install (00:29:19)
In this Nugget, Keith walks you through configuring an IOS router as a Certificate Authority (CA), as well as other routers becoming CA clients that will authenticate and enroll with the CA (using Simple Certificate Enrollment Protocol, SCEP) - in preparation for using their certificates as part of rsa-sig authentication.
This video maps to the "Secure Communications", and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
12. RSA-Sig IKEv2 Authentication (00:19:41)
Using digital certificates, peers who have a a common trusted CA, can authenticate and use the peer's cert and public key to verify the peer's digital signatures for the authentication of the IKEv2 tunnel. In this Nugget, Keith demonstrates this IKEv2 implementation. Supporting files are contained in the NuggeLab download associated with this course.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
13. DVTI IKEv2 Hub and Spoke RSA-Sig (00:16:56)
This Nugget demonstrates how to implement and verify the following: Dynamic Virtual Tunnel Interface (DVTI) on the Hub, Static Tunnel Interfaces on the Spokes, and IKEv2 with RSA-Sig for authentication. Configuration files, including the full final configs, are in the NuggetLab files associated with this course.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
14. IKEv2 Pushing Policy (00:12:51)
Adding network authorization and AAA can allows us to push policy down to VPN peers. This is implemented by creating a new (or modifying the default) IKEv2 authorization policy, and including that IKEv2 authorization policy in the IKEv2 profile.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
15. FlexVPN Clients (00:30:41)
Setting up a spoke as a FlexVPN "Client" allows opportunities for additional features including multiple peers for fault tolerance, and the pushing of networks based on the IKEv2 authorization policy configured. In this Nugget, Keith walks you through reconfiguring the spoke routers to be FlexVPN clients. The use of the IKEv2 authorization profile also is demonstrated to advertise routes between the FlexVPN client and server.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
16. Spoke 2 Spoke FlexVPN (00:32:59)
FlexVPN borrows the Next Hop Resolution Protocol (NHRP) from DMVPN to allow a hub and spoke topology to dynamically build spoke to spoke tunnels. The NuggetLab files contain all the configuration commands used in this video, along with the final working configuration for all four routers.
This video maps to the "Secure Communications," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
17. FlexVPN Troubleshooting (00:20:18)
In this Nugget, Keith walks you through a troubleshooting scenario, leveraging show commands and pings to isolate the problems in a FlexVPN network.
This video maps to the "Troubleshooting, Monitoring, and Reporting Tools" section of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
18. GETVPN (00:50:45)
Group Encrypted Transport VPN (GETVPN) overcomes the delays often associated with creating a spoke-to-spoke tunnel, as there are no formal IPsec tunnels created between group members. In this Nugget, Keith explains and then demonstrates the implementation and verification of GETVPN.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
19. ASA 2 IOS IKEv2 (Site-to-Site IPsec VPN) (00:23:15)
In this Nugget, Keith explains and demonstrates the configuration on the ASA to support both IKEv1 and IKEv2 site-to-site tunnels, as well as configuring a peer IOS router. The router demonstration includes IKEv1 first, with the verification commands to confirm it is working, and then IKEv2 and verification once again that it is working.
This video maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
20. Verify and TShoot IPsec (00:07:29)
In this Nugget, Keith demonstrates where to look inside ASDM to verify or configure the IPsec Site-to-Site configuration implemented from the CLI in the previous video. Note: The following three videos are from the CCNP Security VPN v2.0 course, and it's recommended that you watch them before watching the next Nugget in this course.
ASA VPN Options Site to Site IPsec VPNs Troubleshooting IPsec Site-to-Site VPNs
This video along with the 3 assigned videos map to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
21. RA VPNs (00:12:17)
Remote Access (RA) VPNs play a critical role in secure mobility solutions. In this Nugget, Keith refers to some IOS VPN server documentation that may be useful for administrators of IOS based RA VPNs.
This video includes an assignment of watching the following videos from the CCNP Security VPNv2.0 course: VPN Profiles and Policies; Implementing Clientless SSL VPNs; AnyConnect SSL VPNs; Smart Tunnels and Plugins; AAA VPN Authentication; Troubleshooting Clientless SSL VPNs; Troubleshooting AnyConnect Client SSL VPNs; Cisco Secure Desktop and DAP; High Availability VPNs; and VPN Pieces and Parts.
These videos from the CCNP Security VPN v2.0 course are relevant for real-world experience, as well as the SIMOS 300-209 certification exam from Cisco. The list of assigned videos from this lesson also can be found in the NuggetLab files as a document named "Video Assignment.txt."
This video, along with the assigned videos, maps to the "Secure Communications," "Troubleshooting, Monitoring, and Reporting Tools," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
22. AnyConnect Client Profile (00:14:24)
Whoever thought an XML file could be so powerful? In this Nugget, Keith demonstrates how to modify an AnyConnect Client Profile (the .xml file) on the ASA, and have that profile be automatically downloaded to AnyConnect Clients when they connect. This is an effective way to modify the AnyConnect client profile of remote systems using the ASA as a central distribution point.
This video maps to the "Secure Communications," "Troubleshooting," and "Secure Communications Architectures" sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).
23. Closing Thoughts (00:15:33)
In this Nugget, Keith shares some tips for continued growth and success, along with some troubleshooting strategies.
This video maps to the "Secure Communications" and "Troubleshooting," sections of Cisco's blueprint for Implementing Cisco Secure Mobility Solutions (SIMOS, 300-209).

...